There are no zombies - even though photos from Ashampoo's last Christmas party may suggest otherwise. But the term zombies also describes PCs that are infected with malware and waiting to be remotely controlled. If a cyber criminal manages to infect thousands of machines, he'll own a so-called botnet and will have the means to create a lot of chaos - and make a lot of money. Often, computer owners notice little to nothing of this hostile takeover and that's part of the plan. The longer infections remain undetected, the longer affected machines can be used for murky business. Read on to learn what botnets are, how they're created and what you can do about them.
It all starts with the infection(naturally). If you're a frequent visitor to this blog, you already know how this is usually achieved. Malware gets distributed as email attachments, bundled with pirated software, camouflaged as useful tools or slipped in through security holes in common browsers. If antivirus software fails to notice and stop the attack, these infections will be invisible to you. Malware authors also like to mask signs of infections with so-called rootkits. Originally intended to facilitate system administration, these tools can also be used to suppress all signs of an infection. The final step then is to silently update the malware in the background and often that's the moment the decision on what to (ab)use your PC for is made. There are so many possibilities!
Spam distribution is a classic (and annoying) case. Botnet operators (also called botmasters) contact a large number of infected machines via the Internet, upload mail templates and address lists to the affected devices and off they go. Users may notice a slight increase in hard disk activity or moderate system slowdowns but that's about it. This way, botmasters can send out millions of emails through various IP addresses - it's every spammer's dream and highly profitable, too.
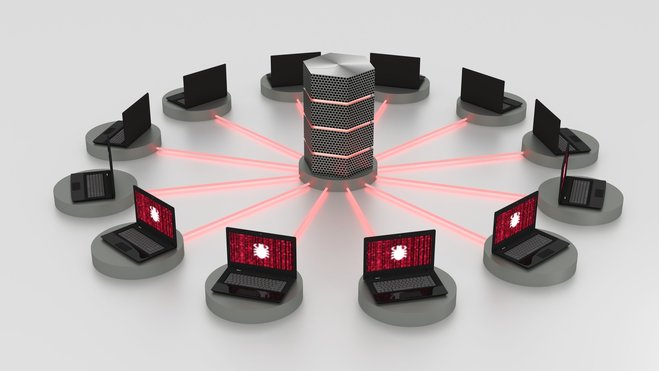
Things take a nasty turn when DDoS (Distributed Denial of Service) attacks come into play. These attacks can bring down entire web sites by sending millions of requests to the affected server until it breaks down. How it works? Here's how. Picture a hotel reception. Receptionists welcome guests, process them and send them to their rooms. A web server does the same. But when the lobby suddenly fills up with 200,000 guests that need immediate information, all hell breaks loose and everything comes to a standstill, think of Hawaii in summer. These attacks frequently serve as leverage in ransom claims against businesses but are also sold to the highest bidder on the black market when businesses try to harm their competition. In recent years, DDoS attacks were often motivated by political protest and directed against companies or political institutions.
Some owners only realize their involvement in a botnet when law enforcement knocks on their doors. That can happen e.g. when illegal content is distributed through affected PCs (file sharing) or when these PCs are used as proxies (relay servers) by the botmaster who will then be sailing under the false flag of the affected PC's IP address. Whatever the attacker then does - it's the PC's IP address that will be visible to the outside world. When the authorities don't investigate thoroughly enough (or simply lack the knowledge and skill for this particular crime), the owner of that PC will be in big trouble even though they are innocent.
Compared to that, advertising fraud is rather unspectacular (but still highly profitable). Some online service providers pay their customers to click on banners, visit particular web sites or to attract visitors to those sites. Once a botmaster unleashes his army of computers to generate thousand of page views or to run scripts that keep clicking on ads, they'll make a nice sum of money. If your botnet consists of over 13 million infected PCs like the "Mariposa" botnet, you'll make millions through this comparatively harmless fraud.

Botnets are also a breeding ground for any other type of Internet crime: sniffers or password grabbers steal your personal information and passwords. Credit card numbers, login credentials for online stores, everything gets stolen. Affected PCs may furthermore fall prey to ransomware. Files are encrypted and users only regain access to their data by paying the ransom - if they're lucky.
If your PC is already affected, you're in deep trouble. Though there are tools that can remove some infections, they are usually so complex, varied and deeply ingrained in your system that it's a difficult procedure with mixed outcomes. Would I happily store my information on such a PC once it has been "cleaned"? I don't know. Backups are a better strategy as your entire system will be reverted to a previous state. Once again, the best approach is to trust the security center between your ears and avoid infections in the first place. Don't install software from unknown sources, don't click on anything on dubious web sites, check email attachments very carefully and stay away from pirated software. If you keep your system up to date and use a decent antivirus solution on top of all that, you should be safe.
Microsoft has set up a page on this topic with tips on how to boost your malware defense: https://www.microsoft.com/en-us/safety/pc-security/botnet.aspx The US department of homeland security is also trying to raise awareness of cyber threats through their "Stop.Think.Connect." campaign: https://www.dhs.gov/stopthinkconnect . Feel free to take a look!




Thank you, yes, very interesting. I have found a positive point with cryptolockers (ransomware), if you want to destroy data on a support for ever and don't want loosing time in formatting dozens of times on it, use a cryptolocker, it will be much faster ;-)
I want to echo the comment/question that Philip Douglas wrote: does malwarebytes give some help?
Sorry for the delayed response! I spent my weekend away from the computer for once. :) Malwarebytes and other similarly good programs have a high detection rate and will find most infections. There’s still a *small* percentage that will go undetected and cause strange system behavior. You can find additional programs and information here: https://www.botfree.eu/en/index.html
Thank you Sven, for another good article .
Very interesting reading. Does Malwarebytes Anti-Malware make it a lot safer for your computer from this type of attack?
Very Interesting and informative, Thank You