We all want data security - and sometimes you need to change your habits for it. I already wrote about strong passwords and how to detect phishing attempts so today's article is about secure logins. Two-factor authentication may sound like a bureaucrat's wet drean but it does wonders for the security of your user accounts, even when your login credentials have already been stolen!

Once others use our credentials to log into Google, Microsoft, Dropbox, Amazon, Apple, Facebook, Twitter and other accounts, there's plenty of room for abuse. At worst, we'll be to our ears in debt because someone went on a shopping spree or the police suddenly turn up at our doorstep because a crime was committed in our name. This is a realistic scenario thanks to trojans, phishing or hacked company servers that store your data. That's why it's all the more important to take additional security measures and two-factor authentication is one of them.
It means that, along with your user name and password, you'll also need to enter a code you received on your cellphone on a case-by-case basis to further prove your identity. This approach effectively locks out anyone who manages to steal your user name and password. You'll need to enable this feature individually for each of your services. Here's how!
-
Log into the affected service with your user name and password.
-
Access your account settings and look for something like "Login settings", "Security" or "Authentication". Each service provider uses different labels, Google calls it "Sign-in & security".
-
Look for an entry similar to "2-step verification" or "Two-Step Verification" and enable this feature.
-
Unless already available, your service provider will now require you to enter your cellphone number.
-
You will then receive a confirmation SMS with a security code. Simply type in your code on your computer and you're good to go. From now on, your cellphone will be part of the login process.
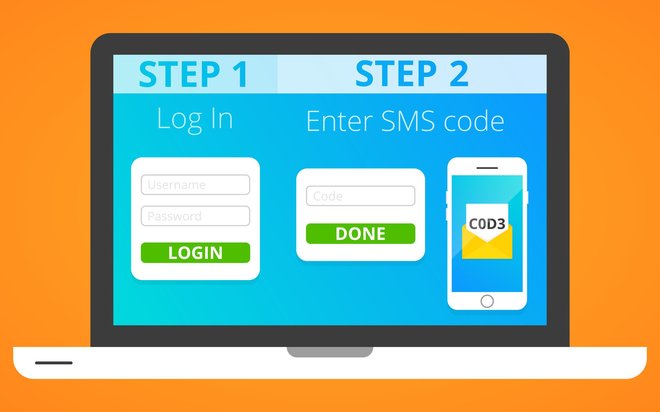
All future logins will now require you to input a code along with your user name and password. It's one more link in your security chain that makes all the difference. Identity thieves that get hold of your login credentials will be permanently locked out. No cellphone, no access, it's that simple! In case you consider the extra step of entering a code for each login too laborious, some providers such as Google allow you to specify secure machines (Add trusted computer) that won't require the code for logins. This way, only login attempts from new and unknown computers will prompt for a code and you won't have to search for your cellphone first when you log into your account at home. But what about vacations or places that don't offer cellphone connectivity? Service providers have you got you covered here, too.
Not only can you receive codes via SMS but you can also generate offline codes Ior later use through special apps like Google Authenticator. Most providers furthermore allow you to add alternative phone numbers or create USB-based authentication keys so that you'll only need to plug in the drive later to pass the extra authentication step. I consider carrying a flash drive around too tedious but some love this approach. If you're a fan of paper-based solutions or prefer a more traditional approach, you'll be delighted to hear you can also print out several codes and use them like you did with TANs in the initial days of online banking.
 Cellphone, security key or paper list, the choice is yours
Cellphone, security key or paper list, the choice is yours
Help on how to set up and use two-factor authentication is available online and providers are putting a lot of effort into making the process as seamless as possible. Note: receiving text messages with codes may create costs, using the various apps is free. As users may be required to reveal their cellphone numbers, this security model may not appeal to everyone and cellphone refuseniks are excluded altogether (though ordinary phones may also work).
If you've been living in constant fear of data theft, you may want to consider two-factor authentication. It doesn't take a lot of getting used to and involves close to zero extra effort once you add your home computer to the list of trusted devices. Finally: the thought that some dirtbag out there has your credentials but can't use them is somewhat appealing, too.
What I would like to know: are you already using two-factor authentication or do you consider using it?




...and what happens if one does not have a cellphone?
There are surprisingly a considerable number of people who do not have one for a whole host of reasons. Privacy. Get away from technology 24/7 etc.
You could also print out code lists like those provided by some banks when online banking started.
Well, how about when your smartphone gets stolen? The thief will have everything needed to log in with TFA, as I guess most people make their smartphone a "trusted device".
Two-factor authentication is supposed to involve two separate devices such as cellphone + stationary PC or tablet.
Hello Sven: I wonder if anything is a secure login. Google and Microsoft force the 2 step login and each gave me about 6 codes for future use. Once done with MS I don't get asked again. I like the way the bank(s) have their set up in Canada. They do offer the two-step verification or an alternative question and answer.
The alternative Q&A in my mind very secure. Who is your favorite musician? Who did you hangout with as a child? No one would know the answers other than me.
It's very intrusive for Google to pin point my location right down to the address. I purchase digital books on Google Play and what does Google do? They make anything I purchase public. I do happen to carry a 1 gig USB stick on my key chain. It's for emergency services to use in case of an accident etc. I know where I would tell Google to put it when I get asked to verify with a code too many times.
To speak on this subject quite honestly then? Files are a subject that seems to have been overlooked. Training makes intelligence apparent and the lack for disciplined study.
Today something wrong occurred to my mother's mobile phone, and it stopped operating. She needed to make a transfer from a bank which required this kind of authentication via mobile. And she needed it urgently before Saturday but it was Fridays's evening already, and all the offices of that bank except just one had been closed (and that's in the capital city of her country!). But imagine it happens to you somewhere abroad - what then? Bad. BTW, I had to deal with this method before the rule was introduced on the EU-scale, and I could not get an SMS (although not from a bank) while in the country different from my mobile operator. The infamous hacking of Yahoo accounts also reminds of the case when strangers get access to your personal data including phone numbers that you have provided. Although you could use a code generator instead of sms, but when you have account in several banks, you wouldn't like to carry many generators instead of one phone. What is really fun is that by attaching you to a mobile connection makes your location and personal routes easier to track - of course, it has nothing to do with e-banking.
Don't own a cell phone get I'm out of luck than huh?
Great!! Not only do these insecure web servers hold my e-mail address and password, they now want my 'phone number too. Just another thing for them to loose to a scammer. Google keeps asking me for a phone number, is this so that can bombard me with adverts via the phone as well as my e-mil??
Once Google, Microsoft or Amazon get hacked, it’s game over anyway. :D This is about probabilities and private data loss occurs far more frequently than customer data being stolen from companies.
This not new... Here in Spain most banks require even more identification, for i.e. wire transfers... I have to enter two codes from a small code card supplied by the banks and, on top of that, I get a sms in my mobile phone asking to enter a third code.
My Master card ask for a special code (sent during the transaction) when I am purchasing something on line so, unless I have my mobile phone handy, I won´t be able to complete the transaction...
In Finland, the bank gives you a code card which you have to enter just to log in... You have to enter the next one in the card everytime you log in...
This is not a new method, it’s been used with online banking for a long time. Google and others are simply slowly following suit and have enabled this type of login only this year. Many users are still unaware of security model which is why we have this article. :)
Two factor authentication might be great for services like online banking, but waiting for, and entering a passcode from my phone, which unlike many people, I don't always have with me (don't need a phone when I have a computer, do I?) is just far too inconvenient. The extra wait and extra work isn't worth the added security, IMHO
окрім коду на СМС ще поставив підтвердження через дзвінок на мобільний телефон для банківських операцій.веб браузер для безпечних розрахунків теж хороша річ:надійніше.
Unfortunately, SMS authentication mechanisms are unsafe due to SS7 and other vulnerabilities. A separate token is probably better. I am thinking, though, of the many financial sites which link together by obligate password sharing - not the using same login passwords, but requiring passwords to bank accounts at credit/budget planning/notification services. Would it perhaps offer somewhat more confidence for banking-type sites to offer two passwords: a master password and a limited, read-balances-only type password?