Those affected may find it quite spooky, either parts of or their entire system is no longer accessible. Instead, they are presented with notifications that can give you goosebumps: A police department is supposed to have found illegal material on their machines. Their copy of Windows is illegal and they need to purchase a license or they have violated copyright laws. Other messages may be more "honest" and will tell mortified users their PCs have been taken over and that their files have been encrypted. They are now required to pay a ransom because they fell victim to ransomware.
Blackmailing through floppy discs
What has become a world-wide phenomenon that now also affects cell phones and doesn't discriminate between Windows and Android devices has its bizarre roots in 1989. Back then, biologist Dr. Joseph Popp sent out 20,000 floppy disks to users across the globe that were supposed to contain the latest information on the then new AIDS disease. Although not free (between $189 and $378) the software was freely installable. Once installed, users were in for a nasty surprise when parts of their files suddenly disappeared and their printers started putting out payment requests for a bank in Panama. Dr. Popp was eventually caught but more then 1000 PCs fell victim to his malware. That was only the beginning.
Ransomware attacks on the rise
While there has been much frenzy over "Locky" in the Spring of this year, things have now fairly quieted down. This is hard to understand as neither Locky (that apparently received an update to better camouflage it) nor the issue itself has gone away. There may no longer be 5000 infections every hour but this is a small comfort for affected users that are now locked out of their PCs. And along with that, the number of affected cell phones this year is steadily rising with a five-fold increase compared to last year. 2015 and 2016 have become the breakthrough years for ransomware affecting both businesses and private users.
An ordinary infection
You can catch ransomware as easily as any other trojan. Drive-by infections are common attack vectors (e.g. visiting a malicious website) as are links embedded in messenger or email messages including Facebook. Naturally, the bad guys know very well that you will be strongly enticed to click and throw caution to the wind when faced with messages such as "Is that you in the picture? How embarrassing!". Flash drives are also vulnerable as well as files from potentially "unsafe" sources such as BitTorrent networks. If you're without security software, you may be in for a world of hurt even if you won't notice it at first.
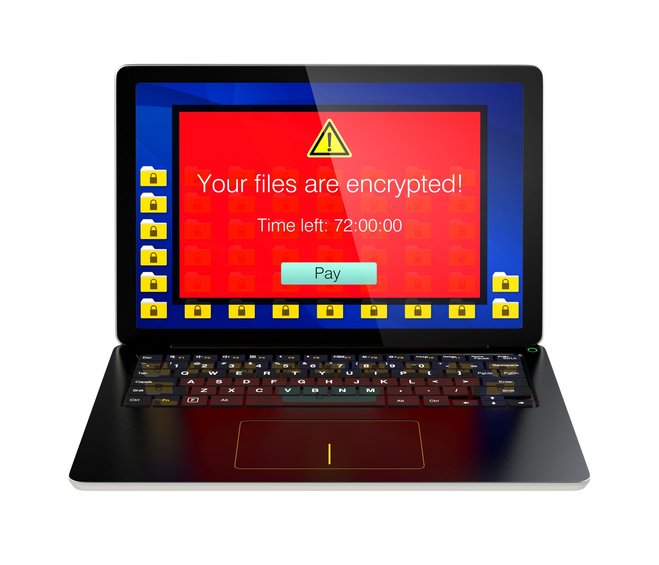
 Suddenly, encryption is the enemy
Suddenly, encryption is the enemy
What happens?
Ransomware authors like to exploit security flaws in common plugins such as Adobe Flash Player, Oracle Java, Adobe Reader and Microsoft Silverlight to install their programs. Once installed, the programs frequently download additional encryption routines and updated payment notices from the Internet. In some cases, they will even download language packs to make sure the victim understands the ransom notice. The program will then start encrypting the files on the host machine - and, alas, it does so quite effectively. Especially personal files will be encrypted with 256-bit keys that are impossible to crack even for the authorities. Some variants will even takes things one step further and encrypt your entire hard disk drives, shutting you out completely.
Should you pay?
Once the damage is done, users will a) be frightened and b) receive a payment notice. A specified amount will have to be paid, usually in Bitcoins (an Internet currency that is nearly impossible to trace, other variants include Paysafecard or Ukash), and then everything will be decrypted again. Whether you should pay is a hotly debated topic. You would give criminals what they want, a rather unpleasant thought, and you would have no guarantee that they will honor the "deal" and give you back access to your machine and files. Still, one German company paid (€490) and was lucky enough to regain access to some of their files. It's not worth the risk unless your life depends on your files. Some experts recommend reporting the attack to the authorities if the chances of success are too slim when viewed realistically.

What can you when it's too late?
I'll be frank with you: There's nothing you can do against (well-programmed) malware that has already taken over your machine. If your files have already been encrypted they are unrecoverable. A glimpse of hope: Kaspersky and Avira have published free recovery discs that may help you in some cases. Live CDs such as Knoppix can help you access files that have not yet been affected without booting into Windows (and triggering further encryption procedures) even when your machine has otherwise been locked. Knoppix is based on Linux, it is free and fairly easy to handle. There may be decryption tools for some (badly programmed) types of ransomware if you're lucky. Try to study the ransom notice carefully to find out who you're dealing with, maybe there's a decryption tool available. If all else fails, there's only one painful way to go: reinstalling your operating system or, in the case of cell phones, performing a factory reset.
How can you protect yourself?
In the same way you can protect yourself against any other type of malware. A decent security software (effective antivirus solution) is a must-have. You should also ensure that your software is up-to-date to close known security holes (frequently exploited by ransomware). Be careful whenever you receive mails or messages from unknown senders and don't just blithely click on embedded links even if they promise to be interesting. Be extra cautious when you're downloading and installing software from unknown source I. While some dubious sites may offer great programs for free, it may cost you dearly later. Regular backups help further safeguard your files and lessen the pain of a forced reinstallation. All these tips also apply to cell phones and tablets that are now also being targeted by ransomware.




As many have said here, a good backup of all your essential files is of the utmost importance. Then ensure it is OFFLINE (removable) so that any encryption software that gets in cannot access or see any on-line volumes or network shares (it infects/encrypts those too). A handy solution for my home desktop is to have a spare HDD installed (plenty of room in a normal desktop case for these, and they are cheap these days) and I use Paragon Hard Disk Manager Pro version 15. It is fine on Windows 10, and it has the added advantage that after doing a full disk clone, it leaves the copy drive HIDDEN (that is, it does not assign a drive letter) so no malware should see it. I copy at least monthly, so I feel protected.
An excellent blog as always, Sven, containing really good advice. Many thanks.
I run a top-rated security package, but you've reminded me that I haven't done a full system image backup on to an external drive for a couple of weeks.
I shall get on with it now!
A worthy blog Sven
My computer experience goes back 30 years. I've seen tears & anger over lost data, sometimes months/years of work lost forever. It's no wonder users pay these criminals. If you use a computer, you must back up your work. For personal users, once per week to at least one external drive & keep it switched off when your working. For business, everyday to 7 different drives if you're open for business 7 days & remember, cell phones are computers with phone access, so backup applies to them also, perhaps more_so. Do this & you can tell the criminals to stick it.
Enjoy your blogs so keep em coming. :-) Philip Burrows
Make full image backups, but make sure the copies are OFFLINE.
There has been more than one instance where the backup is on a LAN connected NAS, and the ransomware has got the backup too.
Thank you sir for an excellent review and knowledgeable information on one of the plagues of computers. This helped tremendously on knowing how to protect computers and what to do in the event hat you become the victim. I did download two of the preventative software's that you listed in your article. I know that like phone solicitation, ransomeware will become a more increasing problem as time passes. I am so glad that there are some like you that take the time and help educated those of us whom do not fully understand the process. Thank you very much, your information is very valuable. Regards, Jay Boutwell. Love your ASHAMPOO software !!
First off, NEVER drop your guard! Kneejerk messages such as "Is that you in the picture? How embarrassing!" are a dead giveaway and I really cannot see how anyone ever falls for stuff like that.
On any modern desktop with 8+GB of RAM, consider virtualisation for your internet connection, only copy across downloads, emails etc. after verification, so if the virtual machine gets infected, it can simply be deleted and a nice clean backup installed in the time it takes to copy a (largish) file.
Another solution is a standalone such as a Raspberry Pi, the V3 is more than potent enough for most internet work, and if the microSD card gets infected, it is dead easy to format it and replace the OS.
Oh, and take even more care when either drunk and/or stoned!
If only I had known your last bit of advice when I was younger … :)
First of all i have all my files backuped on two difrent type of externalflash drive usb and memory card
and i dont keepimportant stuff on pc as they already backed up secend allmy files on sd card and usb are pasword encrypted by me also those who are on my pc to keep themaway from prying exes just in case
2. i already antiransomware protection just in case i was put and setup that toprevent that type of threats
3. ialso setup antivirus and antimalware protection withstrong two way thirdparty firewall
4. i regularry chekup my os and software for updatet and keep themupdated
5. i donot open email fromunknown source and i dont download nothing fromuntrusty source apps and others suff
6.ialso have my os installation backed up as wellmy complete systemimage backup on my pc localy and on sd card
7. and some more stuff i use to secure allmy devices
This is something EVERYONE needs to be aware of and take whatever precautions they can.
Keep your security software up to date, and if you don't have any installed do so AT ONCE.
One great precaution is to image your hard drive often. Now I am NOT a techie, but imaging your hard drive is easy by using one of the several good programs out there.
I use more than one and save them both in the cloud and on external drives. I also do it often, and from time to time just delete the older ones to free up space.
If you don't know what imaging is Google or Bing is your friend. It is much easier to do than one might think.
Good luck and keep your computer safe while on line.
Thank you for that information.
I have found similar things on other persons computers. Saying "you have been found to download illegal software' "you system will be blocked and you will not have access until......) one trick I did, (of course when this happened, it was a pop up, and the screen was blocked.) just go into safe mode, and see if you can access any files, if you can run a program like Malwarebytes, thenn your antivirus. and by doing this, I was able to clear the program.
Now these threats today, may have you completely blocked, but I just wanted to share this.
Excellent article. I backup my more import stuff online but I suppose a good ransomeware program could encrypt that as well.
This is a very good article actually, i'm a programmer and see all kinds of security pitfalls all the time so at the very least you should just be sensible about about your online activity.
@John Everingham - wasn't far wrong there, touch screens can have the links hidden which is really easy as you just turn off the visability which is easy for anyone who wants to steal something from you.
Don't use untrusted sources ie torrents and do have a good security suit, yes we all love free things but many of the free anti virus are simply just not up to the job but as a rule flash is simply an ageing technology which is easily exploited which hopefully will stop being used in the near future.
I don't rely on well known brands for my security needs to protect me, as a programmer i create my own added security but for most people you should just be aware of what you are doing online, protect yourself and your computer and it will save you a headache.
@Howard Rippiner - don't use 3 different anti malware as this makes your system far more insecure than you can imagine and especially don't run them all together as they cancel each other out so take precautions.
Thank you for the great comment!
How timely! Just yesterday, one of my clients was hit by the Zepto virus. Windows Defender is OFF my list of acceptable AV programs for the moment. Trouble is, as hard as they try, A-V vendors just can't keep up. Read on WatchPoint (http://blog.watchpointdata.com) that A-V software is only about 47% effective. I believe it. Too bad we can't track the offenders and fry 'em! Would be a much more effective use of time, effort, and money!
Time to review our security and failure recovery schemas.
I'm surprised how few articles (including this one) on Ransomware talk about the importance of taking complete images of your PC - not just backing up your precious data.
I take a complete new (externally-stored) image (sometimes more than one - using O&O Image Backup or Acronis as well as Windows 10's Imaging routine) every 15-30 days - and certainly after a Windows update - and back up my data to an external encrypted drive every 5-7 days.
If I am unfortunate enough to get 'hit' by ransomware (I run 3 different anti-malware programs so hopefully I won't!), I'll just tell them to get stuffed and re-image my PC - which takes about 40 mins for the C: drive plus the time to put back the data from the external drive.)
Disk images are the most comfortable way to restore your entire system without the hassle of reinstalling. Individual file backups will still save you from the worst. :)
I blame touch screens for the surge in ransom ware.
With a mouse you can see where a link takes you BEFORE you click.
I have seen other ransom ware warnings that describe some ransom ware as 'rootkits' that infect embedded operating systems (typically in phones) and are not removed by the 'factory reset'.
Very good guide to ransomware. Wish I could do without Java and Siverlight. Open source software is safer by nature.