Today, we're getting seriously technical as we are touching one of the holy cornerstones of Windows: The Windows Registry is one of the most delicate (and convoluted) parts of Windows. What it does: Acting as a central repository that stores and provides configuration data for programs, hardware as well as system services and processes. Microsoft apparently doesn't want you to lay hands on it. Read on to learn how to access and modify the Windows Registry anyway.

Opening the Windows Registry
The easiest way to access the Windows Registry is by using the "Run" dialog box. Simply hold down the Windows key and press R to open it. Then, type in "regedit" and click "Ok". Users of Windows 7 and higher may also use the built-in search feature to find the Registry Editor shortcut. The unusual steps required to access the Registry make one thing quite clear - you're not supposed to look behind the curtain.
A first look
Similar to Windows Explorer, Windows Registry entries and hierarchies are displayed as a tree structure. Registry keys (folders) are displayed on the left with their associated name/value pairs (files) in the center. Click the arrow symbols to expand/collapse individual keys. Think of the keys as folders and subfolders and you will find your way around quite easily. Feel free to open a few top-level keys to get a feel for it (don't worry, you won't damage anything).
 Inconspicuous but powerful: Windows Registry
Inconspicuous but powerful: Windows Registry
Root keys
HKEY_CLASSES_ROOT contains all file types that your computer is able to process. Open any of the many entries and you will find a myriad of file extensions (such as ".jpg") with information on their data types (here: image format), the associated viewer program, the default icon and more.
HKEY_CURRENT_USER contains all settings and user permissions for the user that is currently logged in. Windows creates separate entries for each user account (e.g. administrator account, user account, guest account) that store the associated Windows permissions and settings. HKEY_USERS then contains the settings of all users, neatly separated by user name.
HKEY_LOCAL_MACHINE contains all hardware- and driver-related keys including settings that apply to all users. HKEY_CURRENT_CONFIG gets populated at boot time with data from one of the subkeys in HKEY_LOCAL_MACHINE and holds the current hardware configuration.
Anatomy of a Registry key
It's quite straightforward. Each registry key has a name and associated name/value pairs that each can contain various data types (numerical, character-based, hexadecimal etc.) depending on the information they hold. In this case, the name of the entry is "Test", the data type is REG_SZ (a string) and the associated value is "Ashampoo". This pair might for example by used by one of our applications to display the associated text.
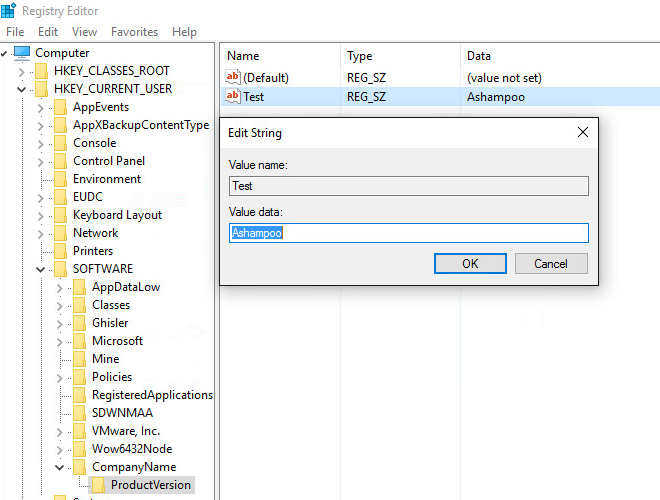
Making changes
You'll usually be forced to access the Registry when single applications or Windows itself malfunction or when you've caught something nasty such as a trojan. Let's assume you have uninstalled an application but the process did not remove all traces of it from your system. Consequently, Windows now searches for files that are no longer there every time it boots up which results in multiple error messages. Turning to Google for help will likely yield a solution that involves modifying or deleting a Registry entry. How do you do it? First, you open Registry Editor as described above. Then, you will have to navigate through the many top-level and nested keys. Example: HKEY_CURRENT_USER\Software\CompanyName\ProductName\Version\ (see above image). First, you need to expand "HKEY_CURRENT_USER", then "Software" and so on until you get to the affected name/value pair, let's call it "Test". Double-click the pair to edit it or right click to bring up the context menu which includes a delete option. You don't have to save your changes afterwards since everything automatically gets written to the Registry and will now apply to your system.
Backups
You can always backup individual keys. Simply select the affected key and either click "File > Export" or use the right-click context menu to create a ".reg" file. You can then import the settings via "File > Import" or by double-clicking the file to restore your original settings. And if you're uncertain about a ".reg" file you can always open it in any text editor to view the associated modifications beforehand.

Warning!
Manipulating the Registry is not without risk which may be one of the reasons Windows does not provide a more sophisticated user interface or even a program shortcut in the task bar. Deleting the wrong keys/pairs may cause nasty errors that can keep programs from working properly or working at all. Beginning with Windows Vista, Microsoft has implemented a protection layer that will prevent the worst (system no longer booting up) but do not take this as a free pass to go on a deletion spree.
Last week´s article: Foreign worlds on Youtube




Super article. Have gathered useful info regarding the subject "Windows Registry". Will make best use of this article during operation of my computer. Just continue furnishing computer lovers with such informative article.Tschuss.
You write the most addicting blog of this or any type. The easy, simple and truth-oriented language demonstrate such a mastery that you can touch with good sense the well washed less educated masses of computer land.
Today's blog was by far the best summary of Windows I have ever read. Do not permit Microsoft to hire you away. They will either be obliged to change their editorial style and rewrite everything technical. OR they can promote you into a highly paid oblivion of conferences, meetings, lunches and non influence.
Every best wish.
Now I do not know what to say. :) Thank you!
Thanks! At last I know a little about the functions of 'The Registry.'
No longer a no go area.
'
Very informative and easy to understand. Thanks.
I still think I will not try modifying it on my computer.
thanks for the information i am just feeling my way around, but will be careful not to delete anything.
richard dunbar
Fantastic article. Thank you for simplifying the task of accessing and modifying this minefield of information.
I have had reason to "tamper" with the registry many times to remove shortcut arrows on desktop icons, remove orphan entries and modify pathways to certain files once I moved the folder to another location.
The Registry no longer scares me, and I have come to embrace it as a silent but busy friend.
Thank you for sharing your knowledge with the rest of us.
Thank you very much. A little bit of praise will brighten up any Monday morning. :)
In the article you mentioned, "Let's assume you have uninstalled an application but the process did not remove all traces of it from your system" I was wondering about your thoughts on certain programs. For example, a few years ago I invested a bit of money into Revo Uninstaller Pro. I've used it with great success but have learned the lessons associated with reading the instructions before using something. I had one problem, which I brought up with the Revo staff, and that was its inability to successfully get rid of a program which was password protected. I failed to remember that I was forced to give the program a password - my bad. The program, Kaspersky, I soon learned to hate and then things got worse until their team helped me out. Now I check each thing that Revo says was left over before I press 'delete'. There are a few others out there that imitate Revo but I would like to know from a 'tech' guy, who is not associated with the program, what he thinks of such programs.
After the first acquisition of a PC accessing the Registry was my main occupation since my curiosity forced this issue. If after opening a file there was a clear indication of what the contents were, then this would make finding a Trojan or malware much easier. Improvements can be made in my opinion, by indicating this with an exclamation mark when such unauthorized material enters the registry. It would make searching for it much easier and would make Technicians redundant from that perspective. They are always too expensive and frequently not up to the task.
very interesting help for windows users